| CPC G06F 21/602 (2013.01) [G06F 13/20 (2013.01); G06F 13/28 (2013.01); G06F 21/57 (2013.01); G06F 21/6218 (2013.01); G06F 21/6281 (2013.01); G06F 21/85 (2013.01); G09C 1/00 (2013.01); H04L 9/32 (2013.01); H04L 63/126 (2013.01); G06F 21/51 (2013.01); H04L 9/0637 (2013.01); H04L 9/3242 (2013.01); H04L 63/12 (2013.01)] | 9 Claims |
|
1. An apparatus comprising:
processor circuitry coupled to a memory;
an input/output (IO) controller to receive a plurality of IO messages from one or more IO devices;
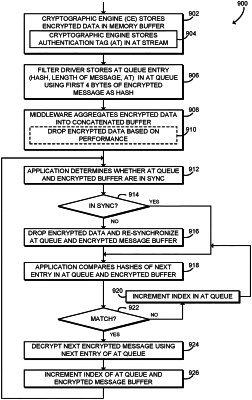
a cryptographic engine configured to perform encryption operations on the plurality of IO messages to generate a respective plurality of encrypted messages and a corresponding plurality of authentication tags (ATs), the cryptographic engine to store the respective plurality of encrypted messages in an encrypted message buffer and to store the corresponding plurality of ATs in an authentication tag queue;
the processor circuitry to execute instructions to:
operate a trusted execution environment (TEE), the TEE to authenticate a next encrypted message of the plurality of encrypted messages based on a comparison with a corresponding AT in the authentication tag queue and, in response to a successful authentication, to decrypt the next encrypted message to generate a decrypted message to be accessible within the TEE;
determine whether the authentication tag queue and the encrypted-message buffer are synchronized; and
drop one or more of the encrypted messages from the encrypted message buffer when the authentication tag queue and the encrypted message buffer are not synchronized, wherein each AT stored in the authentication tag queue comprises one or more of a hash, a message length, or an authentication tag.
|