| CPC G06F 21/602 (2013.01) [G06F 21/54 (2013.01); G06F 21/79 (2013.01)] | 25 Claims |
|
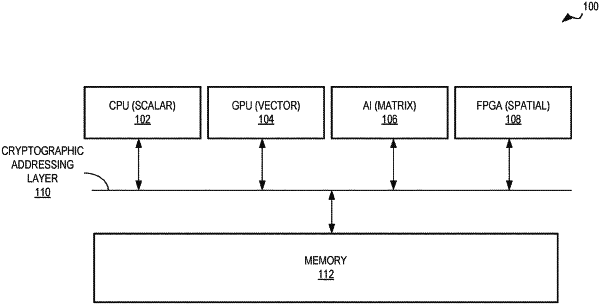
1. A processor comprising:
first circuitry to:
encrypt a first code image using a first code key to generate an encrypted first code image;
load the encrypted first code image into a memory area allocated in memory for the first code image by an operating system running on the processor; and
send to the operating system a substitute key that corresponds to the first code key, wherein the first code key is concealed from the operating system; and
an instruction cache including control circuitry; and
second circuitry coupled to the instruction cache, the second circuitry to:
receive the substitute key from the operating system;
in response to a first request from the operating system to execute the first code image to instantiate a first process, perform a first cryptographic function using a hardware key to generate the first code key from the substitute key; and
program the control circuitry of the instruction cache with the first code key to enable the first code image to be decrypted using the first code key.
|