| CPC H04W 12/122 (2021.01) [H04W 12/02 (2013.01); H04W 12/61 (2021.01); H04W 12/73 (2021.01)] | 16 Claims |
|
1. A method of identifying a malicious access point (AP) by a terminal apparatus, the method comprising:
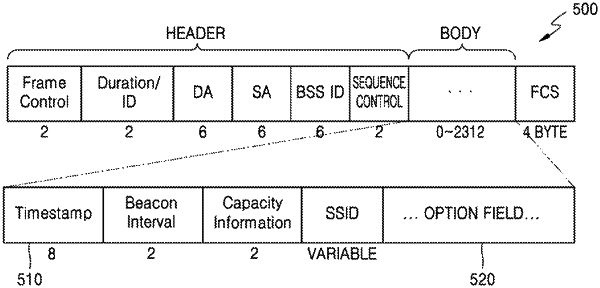
storing information on a first arrangement order of first information elements included in a first beacon signal of a first AP defined as the malicious AP, the first beacon signal including a first header and a first body having a first option field, the first information elements being included in the first option field;
receiving a second beacon signal from a second AP, the second beacon signal including a second header and a second body having a second option field, and second information elements being included in the second option field;
obtaining a second arrangement order of the second information elements included in the second option field of the second body of the second beacon signal by analyzing the received second beacon signal;
comparing the obtained second arrangement order of the second information elements included in the second option field of the second body of the second beacon signal with the first arrangement order of the first information elements included in the first option field of the first body of the first beacon signal; and
identifying the second AP as the malicious AP based on the second arrangement order being the same as the first arrangement order as a result of the comparing.
|