| CPC H04L 9/3268 (2013.01) [H04L 9/0825 (2013.01); H04L 9/3247 (2013.01)] | 11 Claims |
|
1. A method of configuring, generating, issuing, sending, and
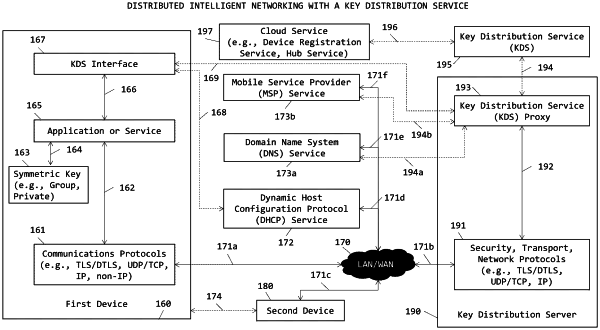
verifying a client certificate to a first device, used in client authentication between applications executing on distributed devices in an Internet of Things (IoT), Industrial IoT (IIoT), or Operational Technology (OT) environment, the method comprising a client application executing on the first device, a server application executing on a second device, a client certificate issued by a certificate authority (CA), a key distribution service (KDS), a KDS portal, a KDS administrator, a KDS proxy, a client KDS interface, a member identifier, a member universally unique identifier (UUID), a member domain name system (DNS) hostname, a symmetric KDS member (M-PSK), a M-PSK identity hint, a tenant identifier, an application identifier, a dynamic host configuration protocol (DHCP) service, and a domain name system (DNS) service:
configuring, on the DHCP service, a vendor class identifier, a scope, and an address pool as an IP address range or a subnet;
configuring, at the KDS portal, a certificate template, a certificate authority (CA) identifier, the first device, a device group, and a device type;
configuring, at the KDS portal, the first device with the device type;
configuring, at the KDS portal, the first device as a member of the device group; and
receiving, by the KDS, a request for a client certificate from the first device at an IP address for a subject name (SN) set as a local identifier of the first device;
generating, by the KDS, a certificate signing request (CSR) with the received subject name (SN) and automatically add X.509 extended attributes in a subject alternate name (SAN), wherein the X.509 extended attributes include an IP address of the first device, a network address and a network mask in the certificate template associated with at least one of the device group or device type of the first device, and an initial identifier of the first device associated with the local identifier of the first device set in the received subject name (SN);
issuing, by the KDS, a client certificate and sending the client certificate to the first device;
authenticating with the KDS, by the client application executing on the first device, using the tenant identifier, the symmetric KDS member (M-PSK), the M-PSK identity hint, and a first DNS hostname, wherein the first device is registered by the first DNS hostname on the DNS service configured with the KDS or the KDS proxy, and wherein the first device is registered as a member device on the KDS;
acquiring, by the client application executing on the first device, a plurality of trusted certificates, the client certificate, and an associated private key from the KDS, using at least the tenant identifier for the plurality of trusted certificates and a subject name for client certificates,
wherein the acquired client certificate and the associated private key is are used in a certificate-based client authentication,
wherein the certificate-based client authentication is executed over a secure transport protocol during communication with the server application executing on the second device, in data signing with digital signatures, or in key unwrapping, and
wherein the certificate-based client authentication provides mutual authentication;
initiating, by the client application executing on the first device, a secure session using a security protocol, wherein the session is initiated using the acquired client certificate and the associated private key providing certificate-based client authentication, establishing secure communications with the server application executing on the second device;
sending, by the client application executing on the first device, the client certificate to the server application executing on the second device, wherein the client certificate is sent during a protocol specific handshake for client authentication;
verifying, by the server application executing on the second device, the IP address of the first device or the subnet, wherein the verifying validates the client certificate based on the X.509 extended attributes in the subject alternate name (SAN) field of the client certificate; and
authorizing the client certificate, by the server application executing on the second device, upon a match of a host address or a network subnet in the client certificate with the IP address of the first device or the subnet, respectively, and continuing with the protocol specific handshake for client authentication.
|