| CPC H04L 9/3247 (2013.01) [H04L 9/0861 (2013.01); H04L 9/0877 (2013.01); H04L 9/14 (2013.01); H04L 9/30 (2013.01); H04L 9/3213 (2013.01); H04L 9/3226 (2013.01); H04L 9/3242 (2013.01); H04L 9/3268 (2013.01); H04L 9/3297 (2013.01); H04L 63/0442 (2013.01); H04L 63/0823 (2013.01); H04W 12/069 (2021.01); H04L 2209/80 (2013.01); H04L 2463/121 (2013.01)] | 16 Claims |
|
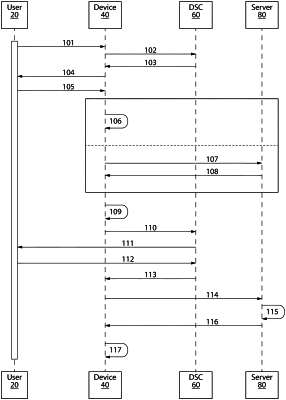
1. A system for digital authentication comprising:
a server;
a device comprising:
a first processor comprising a central processing unit (CPU) configured to provide general processing for the device; and
a second processor separate and distinct from the first processor, the second processor programmed to:
in response to an instruction from the CPU, generate a public key and a private key;
generate at least a first digital signature by:
generating a secret, or receiving a secret from the server;
combining the generated secret and the with other metadata from the device;
generating a device signature comprising device identification information;
combining the combined secret and the device signature to form to-be-signed signature data; and
signing, by the private key, the to-be-signed signature data to generate the first digital signature;
wherein the device is programmed to transmit the public key and the first digital signature to the server;
wherein, after the device transmits the public key and the first digital signature to the server as part of subsequent communication, the device is programmed to generate a second digital signature by repeating the steps for generating the first digital signature;
wherein the device is programmed to transmit the public key and the second digital signature to the server; and
wherein the server is programmed to retrieve using the public key, validate the second digital signature to verify that the second digital signature is from the device or a user of the device, thereby verifying that the subsequent communication is from the device or the user of the device.
|