| CPC H04L 63/1416 (2013.01) [G06N 3/08 (2013.01); H04L 41/0631 (2013.01); H04L 43/04 (2013.01); H04L 61/5061 (2022.05); H04L 63/0227 (2013.01); H04L 63/0236 (2013.01); H04L 63/1425 (2013.01); H04L 63/20 (2013.01)] | 20 Claims |
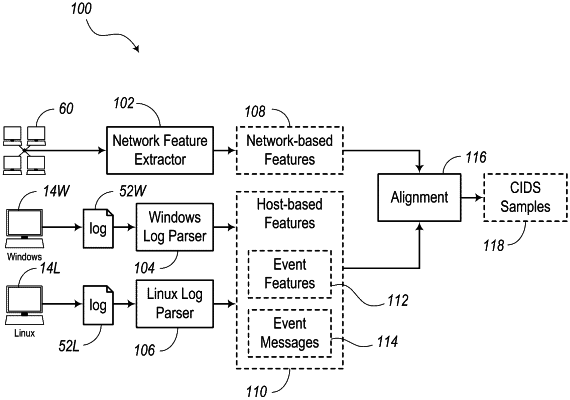
|
1. An Intrusion Detection System (IDS) comprising:
a processing device, and
a memory device configured to store a computer program having instructions that, when executed, enable the processing device to
obtain network traffic information regarding data traffic in a network under observation,
obtain system log information regarding operations of the network under observation,
insert the network traffic information and the system log information into multiple different machine learning analysis procedures, wherein each machine learning analysis procedure of the multiple different machine learning analysis procedures is configured to detect a different sub-attack of a multi-stage attack to which the network under observation is susceptible,
combine the outputs of the multiple different machine learning analysis procedures to detect whether and determine a time period during which one or more sub-attacks have been launched against the network under observation, and
in response to detecting that one or more sub-attacks have been launched during the determined time period, determine the type of the one or more sub-attacks.
|