| CPC H04L 63/1408 (2013.01) [G06F 21/53 (2013.01); G06F 21/567 (2013.01); H04L 63/1416 (2013.01); H04L 63/1425 (2013.01); H04L 63/1433 (2013.01); H04L 63/1441 (2013.01); H04L 63/145 (2013.01); H04L 63/20 (2013.01)] | 18 Claims |
|
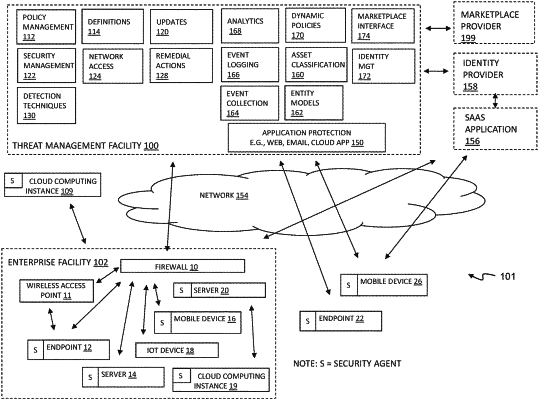
1. A computer program product comprising computer executable code embodied in a non-transitory computer readable medium that, when executing on one or more computing devices, causes the one or more computing devices to perform the steps of:
receiving threat data asynchronously from a plurality of sources, the threat data including at least:
a local threat indication from a local security agent executing on a compute instance in an enterprise network, the local threat indication identifying a category of malicious activity associated with one or more events detected on the compute instance;
geolocation data retrieved from a third-party service for a suspected threat detected on the compute instance; and
cloud resource data based on an action associated with the compute instance at a cloud service supporting one or more cloud-based applications for users of the enterprise network;
in response to asynchronous data from one of the plurality of sources, incrementally calculating a composite threat score indicative of a threat risk for the compute instance based on the threat data;
automatically creating an investigation container when the composite threat score meets a predetermined threshold, the investigation container associated with a user interface for interactively investigating sources of the composite threat score;
displaying the composite threat score to a user in the user interface associated with the investigation container; and
updating the composite threat score in the user interface in response to additional asynchronous data from one of the plurality of sources.
|