| CPC H04L 63/0876 (2013.01) | 20 Claims |
|
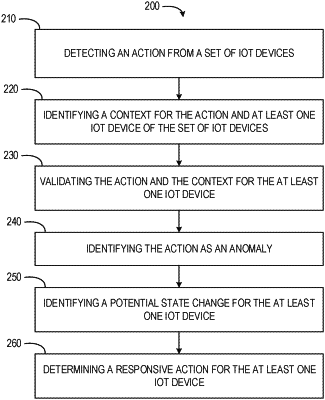
1. A computer-implemented method, comprising:
detecting an action from a set of Internet of Things (IoT) devices;
identifying a context for the action and at least one IoT device of the set of IoT devices;
validating the action and the context for the at least one IoT device;
based on the validating the action and the context, identifying the action as an anomaly;
identifying a potential state change for the at least one IoT device based on the anomaly;
determining whether an allowed tag for the anomaly exists, wherein the allowed tag is based on a usage history of the at least one IoT device and a notification response history for the at least one IoT device; and
determining a responsive action based on the potential state change, existence of the allowed tag, and the anomaly.
|