| CPC G06F 21/563 (2013.01) [G06F 21/554 (2013.01); G06F 21/568 (2013.01); H04L 67/02 (2013.01)] | 25 Claims |
|
1. A non-transitory computer readable medium having stored thereon instructions for filtering content comprising executable code which when executed by processors, causes the processors to:
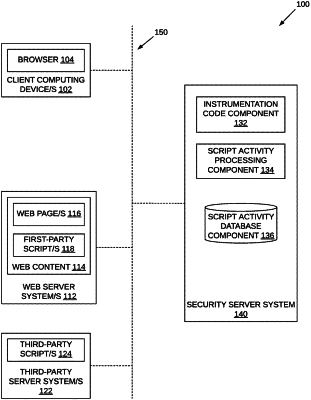
provide instrumentation code for serving to a client computing device with a web page requested by the client computing device, the instrumentation code configured to monitor web code execution at the client computing device when a script referenced by the web page is processed and generate script activity data when the instrumentation code detects script behavior that can exfiltrate data;
receive the script activity data generated by the instrumentation code at the client computing device, the script activity data describing one or more script actions detected by the instrumentation code, wherein the one or more script actions include the script using a Web API interface that enables reading contents of a form field of the web page that is configured to receive data input by a user;
obtain prior script activity data generated by a prior instance of the instrumentation code served with the web page to one or more other client computing devices;
detect a malicious change in the script based on comparing the script activity data and the prior script activity data; and
in response to detecting the malicious change in the script, perform a threat response action.
|