| CPC G06F 21/563 (2013.01) [G06F 21/566 (2013.01); G06F 2221/034 (2013.01)] | 19 Claims |
|
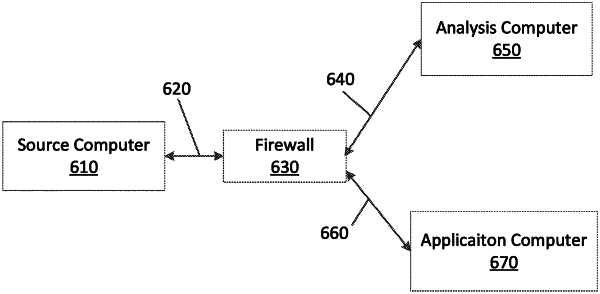
1. A method for analyzing data for suspicious code, the method comprising:
receiving computer information associated with a set of program code, the received computer information including data associated with internal structures of the set of program code;
executing the set of program code, wherein the set of program code is executable to access memory;
identify that the program code is executed to access an allocated region of the memory, wherein the access corresponds to one or more writes to the allocated region;
correlating at least one of the writes to one or more previous writes to the allocated region of the memory based on the data set associated with the set of program code, wherein the correlation includes identifying that at least one of the previous writes has been overwritten in an execution path of one of the writes in the allocated region; and
classifying the program code as suspicious based on one or more suspicious events that include a number of attempts to access and write to the allocated region of the memory, wherein classifying the program code includes matching one or more criteria of an access pattern with the suspicious events associated with malicious program code.
|