| CPC H04W 12/06 (2013.01) [H04L 63/168 (2013.01); H04W 12/08 (2013.01); H04W 12/30 (2021.01); H04L 63/0853 (2013.01); H04L 63/0876 (2013.01); H04W 12/63 (2021.01); H04W 12/68 (2021.01)] | 15 Claims |
|
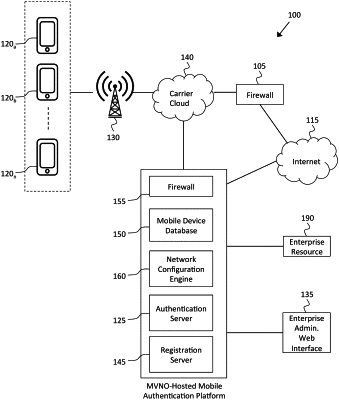
1. A non-transitory computer-readable medium storing instructions that, when executed by one or more computer processors of a server, cause the server to:
receive, from a mobile device, an access request to access a network, wherein the access request includes at least a network identifier of the mobile device;
examine a database of network identifiers assigned to mobile devices for members of the network to determine that the mobile device is used by a member of the network when the identifier of the mobile device is in the database, wherein the network identifier is assigned to the mobile device based on device data of the mobile device and one or more mobile authentication factors of the mobile device;
receive, from the mobile device, a resource request to access a resource within the network;
extract, from the resource request, one or more resource request factors, wherein the extraction includes an inspection of the resource request for a set of permissions for the mobile device by looking up a profile of a user of the mobile device;
authenticate the mobile device based on the set of permissions when the one or more mobile authentication factors respectively correspond with the one or more resource request factors;
determine a location identification of the mobile device, wherein the location identification is determined using cellular triangulation;
compare the location identification with an expected location identification stored in the database; and
provide the authenticated mobile device access to the network in accordance with the set of permission, wherein the mobile device is configured to perform one or more device functions based on the user and a location of the mobile device in one or more coverage areas of the network.
|