| CPC G06F 21/602 (2013.01) [H04L 9/0825 (2013.01); H04L 9/0894 (2013.01); H04L 9/3247 (2013.01); H04L 2209/16 (2013.01)] | 20 Claims |
|
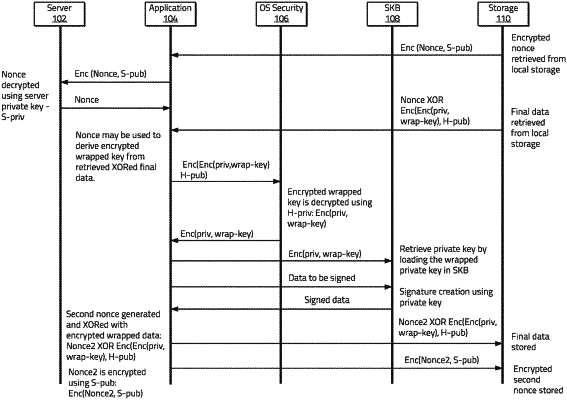
1. A method for performing cryptographic operations by an application executing on a device comprising a processor and a non-transitory computer-readable medium storing instructions that, when executed by the processor, cause the device to perform the method, the method comprising:
retrieving, by the application executing on the device, an encrypted wrapped private key;
sending, by the application to an operating system security service associated with the device, the encrypted wrapped private key for decryption;
receiving, by the application from the operating system security service, a wrapped private key, the wrapped private key being generated by the operating system security service using the encrypted wrapped private key;
sending, by the application to a software cryptographic service associated with the device, the wrapped private key for unwrapping;
sending, by the application to the software cryptographic service, a cryptographic operation request, the cryptographic operation request comprising first data to be operated on by the software cryptographic service; and
receiving, by the application from the software cryptographic service, second data, the second data being generated by the software cryptographic service using the first data and a private cryptographic key generated at least in part by decrypting the wrapped private key.
|