| CPC G06F 21/552 (2013.01) [G06F 21/53 (2013.01); G06F 2221/033 (2013.01)] | 20 Claims |
|
1. A command inspection method performed by a computer device, the method comprising:
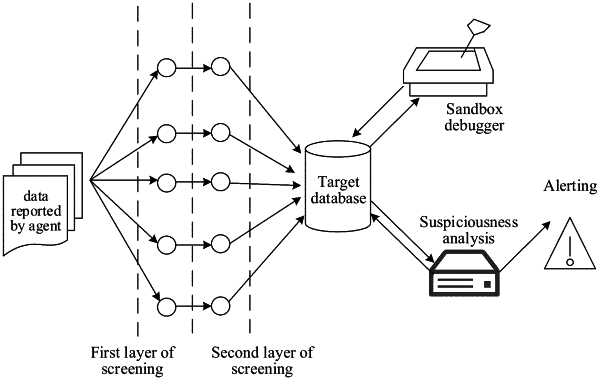
inspecting a plurality of to-be-inspected commands based on a plurality of first features of known obfuscated commands and a plurality of second features of normal service commands, to determine a plurality of target commands, each of the target commands being a command having one or more of the first features but none of the second features;
obtaining running state text of the plurality of target commands, the running state text being textual commands describing operations performed by the plurality of target commands during execution and obtained during a script debugging execution process using a sandbox;
obtaining total suspicious degree information of each of the plurality of target commands, the total suspicious degree information being a total suspicious degree value used for indicating a possibility that the target command is an obfuscated command, including:
obtaining a first suspicious degree value of the target command according to first features matching the target command, each first feature having a corresponding suspicious degree value;
obtaining a second suspicious degree value of the target command according to an extent of a difference between the target command and the corresponding running state text;
adding the first suspicious degree value of the target command and the second suspicious degree value of the target command as the total suspicious degree value of the target command; and
determining, when the total suspicious degree information of any target command satisfies a target condition, the target command as an obfuscated command.
|