| CPC H04W 12/12 (2013.01) [H04L 63/104 (2013.01); H04L 63/14 (2013.01); H04W 4/38 (2018.02); H04W 24/04 (2013.01); H04W 24/02 (2013.01); H04W 84/20 (2013.01)] | 30 Claims |
|
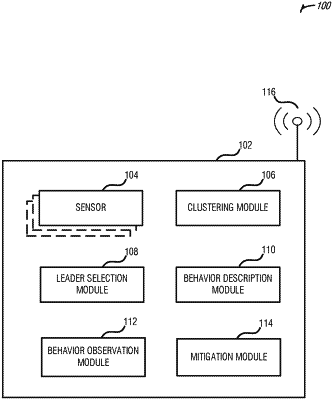
1. At least one non-transitory machine-readable storage device comprising instructions, wherein the instructions, when executed by a processing circuitry of a computing device operable as a primary node in a communication network, cause the processing circuitry to perform operations that:
identify configurations associated with a plurality of network devices arranged as secondary nodes within a cluster in the communication network, wherein the primary node and the secondary nodes are arranged to form the cluster based on physical proximity;
populate the configurations to the secondary nodes using at least one device-to-device communication link within the cluster;
monitor behavior of the secondary nodes within the cluster using the at least one device-to-device communication link;
detect a compromised node of the secondary nodes based on monitoring the behavior and detecting a deviation in at least one of the configurations; and
initiate a mitigation action within the cluster based on detecting the deviation in the at least one of the configurations of the compromised node.
|