| CPC H04L 9/0863 (2013.01) [G06Q 20/3821 (2013.01); G06Q 20/401 (2013.01); H04L 9/3228 (2013.01); H04L 9/50 (2022.05)] | 15 Claims |
|
6. A blockchain based method to conserve processing power and network bandwidth when accounting for missing one time passwords, the blockchain based method comprising:
at a computing platform comprising at least one processor, a communication interface, and memory:
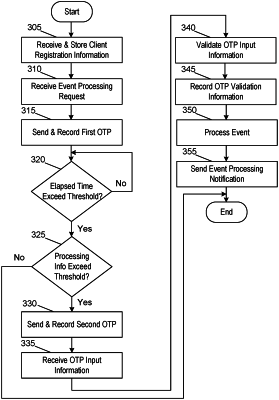
receiving, by the at least one processor, an event processing request;
generating, by the at least one processor, a first one time password;
recording, by the at least one processor, the first one time password in a distributed ledger by adding a new entry to the distributed ledger that includes the first one time password, wherein recording the first one time password using the distributed ledger:
ensures validity of the first one time password,
ensures that the record of the first one time password has been audited, and
ensures that the record of the first one time password is immutable, and wherein the distributed ledger:
is configured to enable smart contracts for event processing requests,
comprises a sequential structure of blocks each storing one of the event processing requests, wherein the event processing requests are sequential in nature and time scale,
comprises one of: a private blockchain or a public blockchain, wherein the public blockchain is encrypted using Rivest-Shamir-Adleman;
sending, by the at least one processor, the first one time password to a first device, wherein the first device is operating on a disrupted cellular network, and wherein the disrupted cellular network prevents receipt of the first one time password by the first device;
identifying that a period of time has elapsed since sending the first one time password to the first device and that the first one time password has not been received at the computing platform from the first device;
identifying that the period of time exceeds a threshold time period;
in response to determining that the period of time exceeds the threshold time period:
generating a second one time password, wherein generating the second one time password is further based on identifying that a trust score corresponding to the first device exceeds a predetermined threshold, wherein the trust score is generated based on a percentage of one time passwords, sent after an initial password and a determination that the period of time has been exceeded, that have been returned to the computing platform from the first device and successfully validated;
recording the second one time password in the distributed ledger;
sending the second one time password to the first device, wherein the first device is configured to:
present an interface prompting for the second one time password to be entered, wherein presenting the interface comprises redirecting the first device from a first website hosted by an enterprise server to a second website hosted by the computing platform, and
receive, via the interface and from a user of the first device, input of the second one time password, wherein receipt of the input of the second one time password causes, based on the redirection of the first device from the first website hosted by the enterprise server to the second website hosted by the computing platform, the second one time password to be communicated to the computing platform;
validating, using the distributed ledger and based on the redirection of the first device from the first website hosted by the enterprise server to the second website hosted by the computing platform, the second one time password, wherein validating the second one time password comprises performing a multi-party validation of the second one time password by the user, an enterprise corresponding to the enterprise server, and an enterprise corresponding to the computing platform;
recording, in the distributed ledger, validation information indicating that the second one time password was validated;
processing, based on validating the second one time password using the distributed ledger, an event corresponding to the event processing request; and
sending, by the at least one processor and to the first device, a notification indicating that the event was processed and one or more commands directing the first device to display the notification indicating that the event was processed, wherein sending the one or more commands directing the first device to display the notification indicating that the event was processed causes the first device to display the notification indicating that the event was processed and that the second one time password was validated using the distributed ledger.
|