| CPC H04L 9/0861 (2013.01) [H04L 63/1466 (2013.01); H04L 67/02 (2013.01)] | 24 Claims |
|
1. A method comprising:
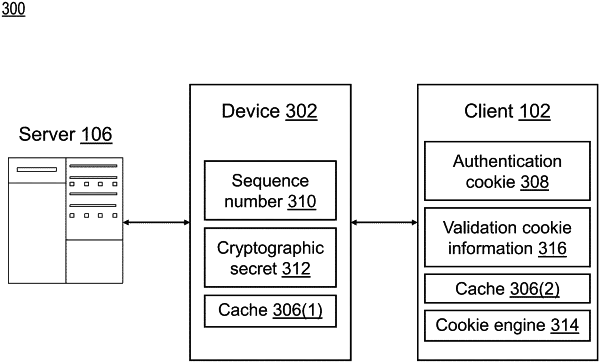
receiving, by a client via a device, an authentication cookie for access to a server, the device maintaining a sequence number and a cryptographic secret;
receiving, by the client from the device, a cookie engine, the cookie engine being executable code that when executed generates validation cookie information;
generating, by the client using the cryptographic secret and the cookie engine, validation cookie information with an updated sequence number increased by the client by a predetermined defined value responsive to generating the validation cookie information; and
sending, by the client to the device via a hypertext transfer protocol (HTTP) message, the authentication cookie, and the validation cookie information with the updated sequence number to validate the authentication cookie.
|