| CPC H04L 63/1425 (2013.01) [G06F 9/455 (2013.01); G06F 9/545 (2013.01); G06F 16/9024 (2019.01); G06F 16/9038 (2019.01); G06F 16/9535 (2019.01); G06F 16/9537 (2019.01); G06F 21/57 (2013.01); H04L 43/045 (2013.01); H04L 43/06 (2013.01); H04L 63/10 (2013.01); H04L 67/306 (2013.01); H04L 67/535 (2022.05); G06F 16/2456 (2019.01)] | 20 Claims |
|
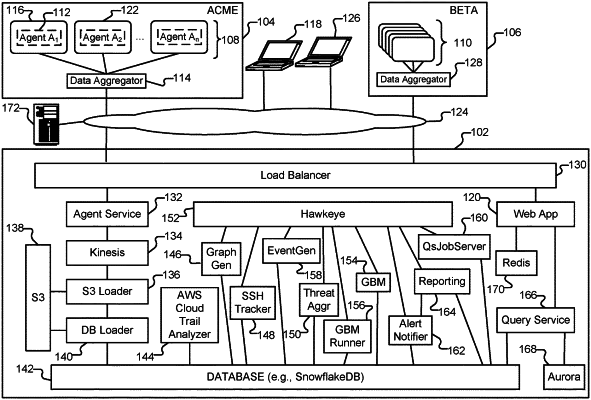
1. A method comprising:
generating, based on log data associated with at least one user session in a network environment associated with a user, a logical graph, wherein the logical graph comprises: (1) a first node corresponding to the user, (2) a plurality of additional nodes, and (3) a set of edges connecting the first node to one or more of the additional nodes, wherein each edge in the set of edges represents a change in behavior of the user;
using the logical graph to detect an anomaly, wherein detecting the anomaly includes determining that a change has been made to at least one edge included in the set of edges; and
generating, in response to detecting the anomaly, an alert.
|