| CPC H04L 63/1425 (2013.01) [H04L 43/08 (2013.01); H04L 47/286 (2013.01); H04L 47/827 (2013.01); H04L 61/5007 (2022.05); H04L 63/126 (2013.01); H04L 63/1416 (2013.01); H04L 63/1466 (2013.01)] | 20 Claims |
|
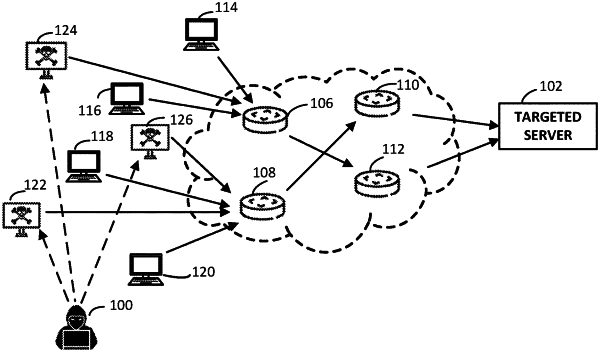
1. A computing system for coupling to a computer network, the computing system having resources for processing data packets received from the computer network, the data packets having headers that include a source IP address value (SrcIP) and a Time to Live value (TTL), the computing system comprising traffic management apparatuses, client devices, or server devices, the computing system comprising memory comprising programmed instructions stored thereon and processors configured to be capable of executing the stored programmed instructions to:
receive data packets from the network and configured to extract the SrcIP value from the header of each data packet;
use the SrcIP value to look up a corresponding geo-location from which the received data packet was purportedly sent by searching a look-up table indexed by the SrcIP;
determine whether the corresponding geo-location is a country or region from which resource attacks are frequently mounted and whether a reverse path leads back to the corresponding geo-location from which the received data packet was received; and
in response to determining the corresponding geo-location is a country or region from which resource attacks are frequently mounted and that the reverse path fails to lead back to the corresponding geo-location, increase the probability that a received data packet was initiated by an attacker mounting a resource attack against the computing system.
|