| CPC G06F 21/56 (2013.01) [G06F 21/554 (2013.01); G06F 21/6209 (2013.01); H04L 61/4511 (2022.05); H04L 63/1491 (2013.01); G06F 2221/2111 (2013.01); G06F 2221/2129 (2013.01)] | 16 Claims |
|
1. A computer-implemented method comprising:
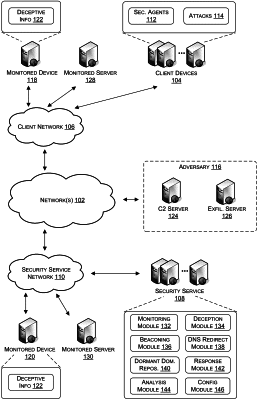
receiving a domain name resolution request from a requesting process operating on a device;
determining that a domain name included in the domain name resolution request is indicative of malicious activity;
responding to the domain name resolution request with a network address of a monitored server posing as an adversary server associated with the requesting process to prompt an adversary communication to the monitored server instead of the adversary server;
transitioning an attack associated with the requesting process from the device to the monitored server;
monitoring activities of the attack on the monitored server;
enabling the monitored server to load deceptive information onto a memory of the monitored server; and
enabling an attacker associated with the attack to acquire the deceptive information from the monitored server through the adversary communication.
|