| CPC G06F 21/554 (2013.01) [G06F 18/21 (2023.01); G06F 18/2431 (2023.01); G06F 21/31 (2013.01); G06N 5/04 (2013.01); G06N 20/20 (2019.01); G06V 10/25 (2022.01); G06V 10/82 (2022.01); G06V 20/41 (2022.01); G06V 20/52 (2022.01); G06V 30/19173 (2022.01); G06V 30/274 (2022.01); G08B 13/19613 (2013.01); G08B 29/188 (2013.01); H04N 23/90 (2023.01); G06Q 50/265 (2013.01); G06V 20/44 (2022.01)] | 19 Claims |
|
1. A method, comprising:
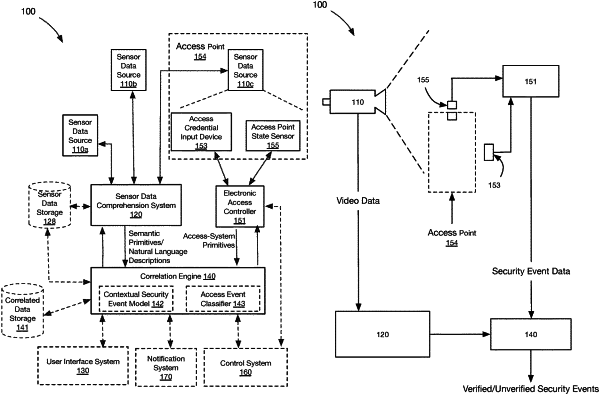
determining a set of access primitives based on a first set of signals from an access point state sensor;
determining a set of authorization primitives based on a second set of signals from a security credentialing system;
determining a set of semantic primitives based on a third set of signals from a camera system;
determining a correlation between the set of access primitives, the set of semantic primitives, and the set of authorization primitives;
determining a context classification based on the correlation; and
based on the correlation, determining a security risk associated with the context classification.
|