| CPC H04L 63/145 (2013.01) [G06F 18/214 (2023.01); H04L 51/08 (2013.01); H04L 63/1416 (2013.01); H04L 63/1483 (2013.01)] | 20 Claims |
|
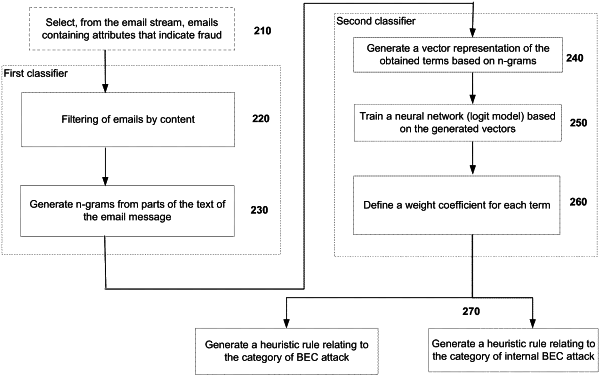
1. A method for creating a heuristic rule based on received email messages to identify Business Email Compromise (BEC) attacks, the method comprising:
filtering text of received email messages, using a first classifier, to extract one or more terms indicative of a BEC attack from the text of the received email messages, wherein the first classifier includes a trained recurrent neural network that includes a language model;
generating, using the first classifier, one or more n-grams based on the one or more extracted terms, wherein each of the one or more n-grams characterizes a particular extracted term;
generating, using a second classifier, a vector representation of the one or more extracted terms based on the generated one or more n-grams;
assigning a weight coefficient to each of the one or more extracted terms, wherein a higher weight coefficient indicates higher relevancy to BEC attack of the corresponding extracted term; and
generating a heuristic rule associated with the BEC attack by combining the weight coefficients of a combination of the one or more extracted terms.
|