| CPC H04L 63/1425 (2013.01) [H04L 63/1466 (2013.01)] | 18 Claims |
|
1. A threat actor identification system comprising:
a computer embodying a threat actor identification system, the computer comprising at least one processor and at least one non-transitory computer-readable medium storing instructions translatable by the at least one processor to perform:
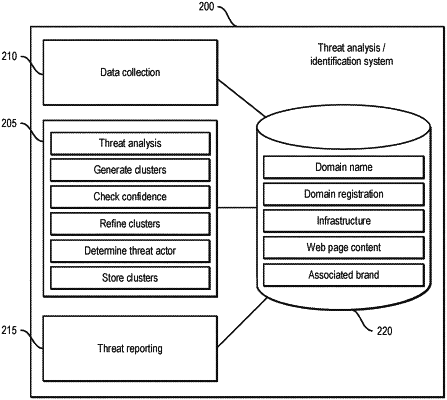
obtaining domain data for each of a plurality of domains;
generating, based on computed similarities in the obtained domain data, one or more domain clusters, each domain cluster including a corresponding subset of the plurality of domains, wherein the generating of the one or more domain clusters is based on an examination of the obtained domain data, which includes:
examining web page content for the plurality of domains, determining web page content similarity values indicative of similarities between individual ones of the plurality of domains, and generating domain clusters based on the web page content similarity values; and
examining infrastructure data for the plurality of domains, determining infrastructure data similarity values indicative of similarities between individual ones of the plurality of domains, and generating domain clusters based on the infrastructure data similarity values;
determining, for one or more of the generated domain clusters, that the domain cluster is associated with a threat actor; and
providing, for the one or more of the generated domain clusters that is associated with the threat actor, an indication of the corresponding threat actor to one or more corresponding entities targeted by the threat actor.
|