| CPC H04L 63/108 (2013.01) [G06F 21/00 (2013.01); G06F 21/335 (2013.01); G06F 21/6218 (2013.01); H04L 63/068 (2013.01); H04L 63/0807 (2013.01); H04L 63/083 (2013.01); H04L 63/0876 (2013.01)] | 15 Claims |
|
1. A method for securing ordered resource access of an initial and an additional resource, the method comprising:
receiving, at a service provider over a network, a request for the initial resource from a client device;
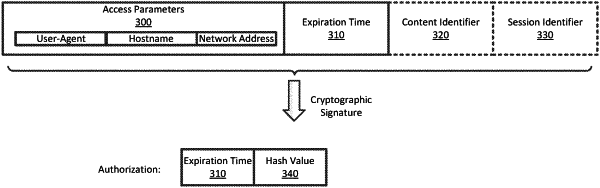
identifying access parameters of the request for the initial resource, wherein the access parameters are identifiable for a future request from the client device for the additional resource at a resource provider, wherein the access parameters comprise a hostname designated in the request for the initial resource, a user-agent designated in the request for the initial resource, a network address originating the request for the initial resource, a content identifier specific to a content item or a group of content items of the additional resource, a session identifier that describes a session token or session information for the client device, and a salt for a cryptographic signature, such that at least one parameter of the cryptographic signature is not accessible by the client device;
generating, by the service provider, a token for the request, the token derived by applying the access parameters to a hash function using a secret key, the secret key shared with the resource provider over the network for authorizing requests for the additional resource;
providing the token to the client device for inclusion by the client device in the future request for the additional resource, the future request authorized by the resource provider, using the token, by applying the access parameters in the future request to the hash function using the secret key to confirm whether the initial resource was first provided to the client device by the service provider; and
generating, based on the access parameters and a risk score of the client device, an authorization including an authorization token for access to the additional resource, wherein the authorization token encodes the token and an expiration time,
wherein when the content identifier is used, a different authorization is generated for each additional content item to be accessible by the client device.
|