| CPC H04L 63/107 (2013.01) [H04L 63/08 (2013.01)] | 8 Claims |
|
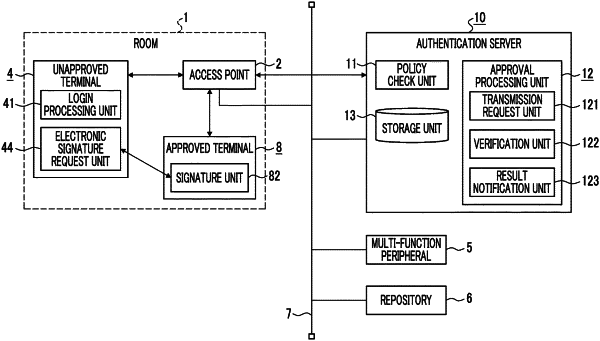
1. An authentication system comprising:
an authentication server that has a first hardware processor and authenticates users who use terminals to which login requests for a network system have been transmitted;
a first terminal that has a second hardware processor and is used by a user who is not permitted to log into the network system, wherein the first terminal receives a login request and the second hardware processor is configured to transmit the login request received by the first terminal to the authentication server through an access point for requesting a login process to a network, wherein the login request transmitted from the first terminal is modified by the access point by attaching an identification of the access point to the login request, and
a second terminal that is used by a user who is permitted to log into the network system;
wherein the first hardware processor is configured to:
receive the login request from the first terminal and the identification of the access point attached to the login request and in response to the login request from the first terminal, transmit a request including authentication information to the first terminal requesting the first terminal to transmit proof information for proving that the first terminal is located in a specific space,
receive proof information including authentication information from the second hardware processor;
verify whether the first terminal is located in the specific space with the second terminal on the basis of identification of the access point and verification of whether the received proof information is verified as generated by the second terminal and transmitted from the first terminal and permit the first terminal to log into the network system when verification of the first terminal is successful; and
deny the first terminal permission to log into the network system when the authentication data included in the request for proof information does not match the authentication data in the received proof information.
|