| CPC H04L 63/0838 (2013.01) [G06F 21/35 (2013.01); G06F 21/36 (2013.01); H04L 9/3228 (2013.01); H04L 9/3234 (2013.01); H04L 9/3268 (2013.01); H04L 63/061 (2013.01); H04L 63/08 (2013.01); H04L 63/0853 (2013.01); H04Q 5/22 (2013.01); H04W 12/06 (2013.01); H04W 12/068 (2021.01); H04W 12/35 (2021.01); G06F 15/173 (2013.01); H04W 12/77 (2021.01); H04W 88/02 (2013.01)] | 20 Claims |
|
1. A computer-implemented method, comprising:
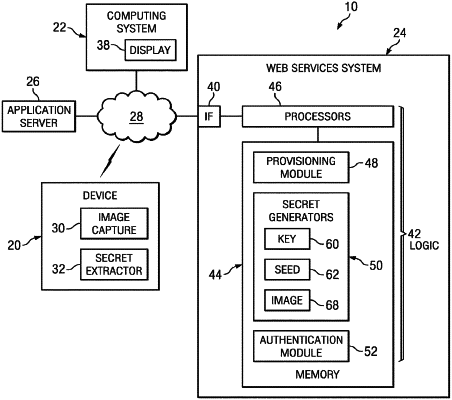
causing a computing device to capture an image displayed on a first system, wherein the image is obtained from a second system as a result of the first system submitting a request to the second system through a first communication channel to generate the image;
determining a challenge code from the image;
generating a response based at least in part on the challenge code and a first authentication information, wherein the first authentication information is obtained by the computing device in response to the computing device transmitting an encryption key generated based on another image to the second system; and
submitting, from the computing device, the response to the second system through a second communication channel, different from the first communication channel, to verify the computing device to perform one or more operations provided by the second system.
|