| CPC H04L 63/08 (2013.01) [G06F 9/44505 (2013.01); H04L 9/0822 (2013.01); H04L 9/085 (2013.01); H04L 9/0894 (2013.01); H04L 9/14 (2013.01); H04L 9/3226 (2013.01); H04L 63/0428 (2013.01); H04L 63/06 (2013.01); H04L 63/083 (2013.01); H04L 63/107 (2013.01); H04L 63/108 (2013.01); H04L 63/1466 (2013.01); H04W 12/041 (2021.01); H04W 12/0431 (2021.01); H04W 12/06 (2013.01); H04W 12/086 (2021.01); H04L 2209/80 (2013.01)] | 20 Claims |
|
1. A method comprising:
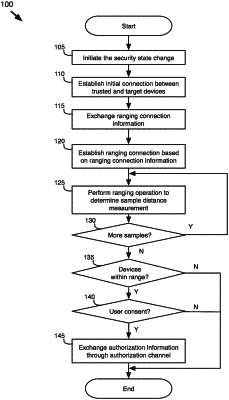
detecting, by a first device, an announced availability of a second device for modifying a security state at the first device;
exchanging, by the first device and using a first wireless protocol, ranging connection information with the second device;
performing, by the first device, using a second wireless protocol and based on the ranging connection information, a ranging operation with the second device to estimate a distance between the first and second devices; and
in response to determining that the distance satisfies a distance threshold, establishing, by the first device and using the first wireless protocol, a connection with the second device for modifying the security state at the first device.
|