| CPC H04L 63/0428 (2013.01) [G06F 16/334 (2019.01); G06F 16/951 (2019.01); H04L 9/0631 (2013.01); H04L 9/0825 (2013.01); H04L 9/0869 (2013.01); H04L 9/0891 (2013.01); H04L 9/0894 (2013.01); H04L 63/0807 (2013.01); H04L 63/0823 (2013.01); H04L 63/083 (2013.01)] | 20 Claims |
|
1. A computer-implemented method performed by a client device, the method comprising:
receiving search terms from a user;
tokenizing the search terms into a first set of tokens;
adding one or more decoy tokens to the first set of tokens to obtain a second set of tokens;
transforming the second set of tokens to generate at least one set of transformed tokens, wherein transforming the second set of tokens comprises:
identifying a plurality of possible salt values for the second set of tokens, the plurality of possible salt values comprising at least one of (i) a plurality of salt values corresponding to different time periods or (ii) a plurality of salt values derived from user identities, message identities, or conversation identities; and
generating the at least one set of transformed tokens by, for each possible salt value of the plurality of possible salt values, transforming the second set of tokens using the possible salt value;
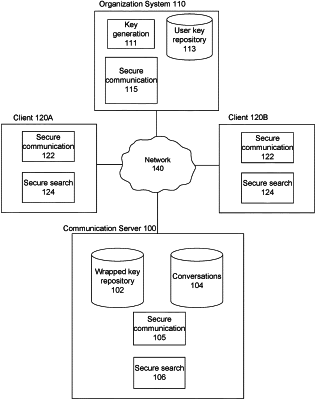
sending the at least one set of transformed tokens to a communication server for identification of matching messages from a plurality of messages stored by the communication server, wherein the communication server comprises a search index comprising one or more transformed tokens corresponding to each message from the plurality of messages;
receiving from the communication server a set of messages matching the at least one set of transformed tokens, wherein the set of messages comprises at least one false positive match resulting from the decoy tokens; and
filtering out the at least one false positive match from the set of messages by comparing the set of messages with the search terms.
|