| CPC H04L 63/0245 (2013.01) [H04L 12/4633 (2013.01); H04L 12/66 (2013.01); H04L 63/0263 (2013.01)] | 17 Claims |
|
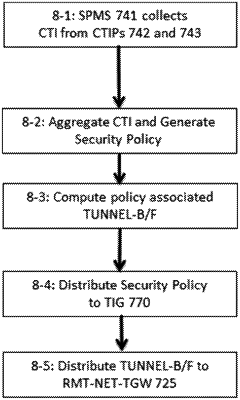
1. A method for selectively filtering traffic of a remote network by tunneling portions of that traffic to a central network to be filtered by the central network, the method comprising:
receiving, by a security policy management server at the central network, threat information from a plurality of different independent cyber threat intelligence providers;
generating, by the security policy management server and based on the threat information, a plurality of packet filtering rules of a security policy, wherein each of the plurality of packet filtering rules of the security policy comprises one or more packet matching criteria and corresponding rule actions to take on packets matching the packet matching criteria;
generating, by the security policy management server, a policy probabilistic data structure that represents each of the plurality of packet filtering rules of the security policy;
sending, by the security policy management server and to a remote network tunnel gateway at the remote network, the policy probabilistic data structure;
receiving, from the remote network tunnel gateway and via a tunnel between the remote network and the central network, a packet, wherein the remote network tunnel gateway sent the packet via the tunnel based on a determination that a first packet matching criterion of the packet was represented in the policy probabilistic data structure; and
filtering the packet based on the plurality of packet filtering rules of the security policy, wherein filtering the packet based on the plurality of packet filtering rules of the security policy comprises filtering the pack et in accordance with one or more rule actions.
|