| CPC H04L 63/0236 (2013.01) [H04L 63/1425 (2013.01); H04L 63/1458 (2013.01)] | 24 Claims |
|
1. A packet-filtering device comprising:
one or more processors; and
memory storing instructions that, when executed by the one or more processors, cause the packet-filtering device to perform:
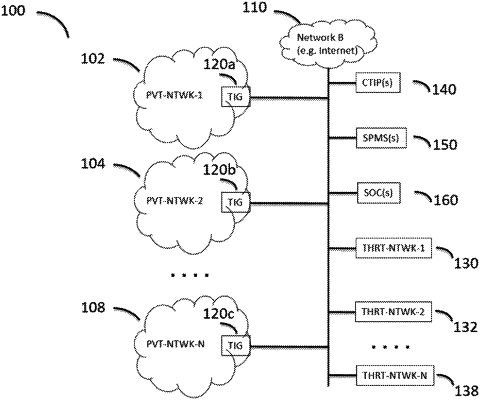
receiving a plurality of packet-filtering rules configured to cause the packet-filtering device to identify packets corresponding to at least one of a plurality of threat indicators, wherein the plurality of packet-filtering rules was generated based on a plurality of cyber threat intelligence reports from one or more cyber threat intelligence providers, wherein the plurality of cyber threat intelligence reports comprises the plurality of threat indicators, and wherein the plurality of threat indicators comprises a plurality of network addresses;
determining an occurrence of an incident;
receiving, during the incident, a plurality of packets that match at least one of the plurality of packet-filtering rules, wherein the plurality of packets are in a plurality of flows associated with the incident;
based on a first one or more flows, of the plurality of flows, that causes one or more transmission control protocol (TCP) flow state transitions, generating flow log data associated with the first one or more flows;
based on a second one or more flows, of the plurality of flows, that does not cause any TCP flow state transition, generating incident log data associated with the second one or more flows;
sending the flow log data associated with the first one or more flows; and
sending, in lieu of flow log data associated with the second one or more flows, the incident log data associated with the second one or more flows.
|