| CPC G06Q 20/3829 (2013.01) [G06Q 20/352 (2013.01); G06Q 20/38215 (2013.01); H04L 9/0838 (2013.01); H04L 9/0866 (2013.01); H04L 2209/56 (2013.01)] | 20 Claims |
|
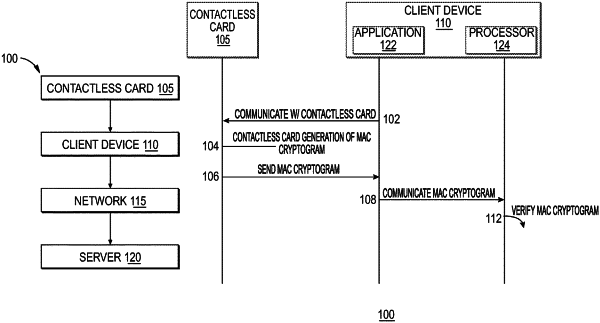
1. A system, comprising:
a contactless card having a processor and memory, the memory of the contactless card containing a card key and transmission data;
an application comprising instructions for execution on a receiving device having a processor and memory, the memory of the receiving device containing an application key;
wherein the contactless card is configured to:
encrypt the transmission data using a cryptographic algorithm and the card key to yield encrypted transmission data, and
transmit the encrypted transmission data to the application; and
wherein the application is configured to:
decrypt the encrypted transmission data using the cryptographic algorithm and the application key;
authenticate a user identity associated with a user;
record information comprising at least one selected from the group of a time of authentication, a location of authentication, a type of contactless card, a type of receiving device, a movement of one or more entries into a communication field, and a timing of one or more entries into a communication field; and
after authenticating the user identity, access sensitive information.
|