| CPC G06Q 20/3821 (2013.01) [G06Q 20/3226 (2013.01); G06Q 20/3229 (2013.01); G06Q 20/3829 (2013.01)] | 20 Claims |
|
1. A computer-implemented method, comprising:
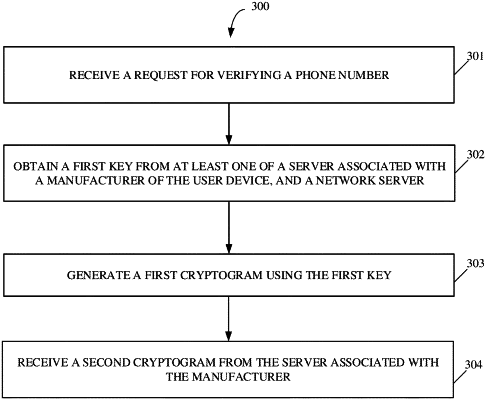
receiving, by at least one server, a request for a key from a user device in response to the user device receiving a request for verifying a phone number associated with a Subscriber Identification Module (SIM) card in the user device from a merchant application of the user device, the request for verifying the phone number being received by the user device in response to a selection of a payment card of a plurality of payment cards stored in the merchant application for a payment transaction between a user of the user device and a merchant associated with the merchant application;
communicating, by the at least one server, the key to the user device in response to receiving the request for the key, wherein communicating the key comprises one of:
communicating a first key to the user device, the first key generated by the at least one server in real-time using one or more cryptographic techniques, wherein the key comprises the first key;
communicating a second key to the user device, the second key generated by the at least one server and stored in a memory associated with the user device during manufacturing of the user device, wherein the key comprises the second key; or
communicating the request for the key to at least one other server,
receiving a third key from the at least one other server, and communicating the third key to the user device, wherein the at least one other server generated the third key in real-time using the one or more cryptographic techniques, wherein the key comprises the third key;
receiving, by the at least one server, a first cryptogram generated based on the phone number using the key and a safety attestation certificate indicating integrity of the user device from the user device;
verifying, by the at least one server, the first cryptogram and the safety attestation certificate; and
communicating, by the at least one server, a second cryptogram to the user device, wherein the second cryptogram and payment transaction details are provided by the merchant application to an issuer server for authentication of the payment transaction.
|