| CPC G06Q 20/3674 (2013.01) [G06F 21/30 (2013.01); G06F 21/44 (2013.01); G06Q 20/3227 (2013.01); G06Q 20/3278 (2013.01); G06Q 20/3672 (2013.01); H04L 9/3236 (2013.01); H04W 12/63 (2021.01)] | 20 Claims |
|
1. A method comprising:
generating, by a server computer, a first cryptographic pattern by hashing at least a credential or token, and a nonce;
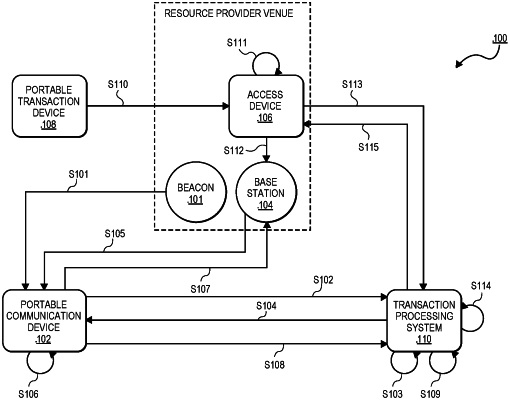
sending, by the server computer to a portable communication device of a user, the first cryptographic pattern and the nonce, causing the portable communication device to perform scanning for nearby base stations and receive a base station identifier from a base station, the base station identifier comprising a universally unique identifier (UUID), wherein the portable communication device transmits the nonce to an access device via the base station;
receiving, by the server computer and from the portable communication device of the user, the base station identifier, the base station identifier comprising the universally unique identifier (UUID) uniquely identifying a resource provider location;
generating, by the server computer, a second cryptographic pattern, by hashing, by the server computer, at least the first cryptographic pattern and the base station identifier;
storing, by the server computer, the second cryptographic pattern;
receiving, by the server computer, from the access device in a transaction, an authorization request message comprising the second cryptographic pattern, after the access device forms the second cryptographic pattern by receiving the credential or token from a portable transaction device of the user, forming the first cryptographic pattern by hashing the credential or token, and the nonce, and then forming the second cryptographic pattern by hashing the first cryptographic pattern and the base station identifier comprising the universally unique identifier (UUID);
analyzing, by the server computer, the authorization request message by determining that the user of the portable communication device and the portable transaction device are conducting the transaction at the access device by determining that the second cryptographic pattern in the authorization request message matches the second cryptographic pattern stored by the server computer; and
at least in response to determining that the second cryptographic pattern in the authorization request message matches the second cryptographic pattern stored by the server computer, transmitting, by the server computer an authorization response message to the access device indicating that the transaction is approved, wherein the portable communication device, the base station, the user, and the portable transaction device are within the resource provider location which is a merchant store.
|