| CPC G06F 8/63 (2013.01) [G06F 8/433 (2013.01); G06F 16/90344 (2019.01); G06F 21/577 (2013.01); G06F 9/45558 (2013.01); G06F 2009/4557 (2013.01); G06F 2009/45587 (2013.01)] | 20 Claims |
|
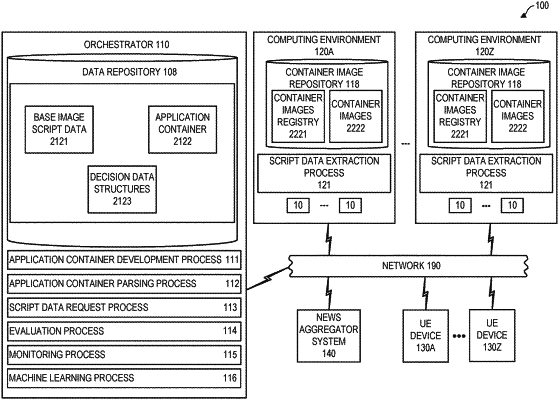
1. A computer implemented method comprising:
examining target application container configuration data to identify one or more target container base image referenced in the target application container configuration:
subjecting script data associated to the one or more target container base image to text based processing, wherein the text based processing comprises a text string associated with a confidence level, for evaluation of security risk associated to the one or more target container base image, the script data obtained from at least one candidate hosting computing environment;
selecting a hosting computing environment from the at least one computing environment for hosting a target application container, the selecting in dependence on the text based processing; and
iteratively performing the text based processing for evaluation of security risk and the selecting the hosting computing environment, wherein the method includes hosting the target application container on a first computing environment, and re-hosting the target application container on a second computing environment having a threshold satisfying a security performance level, responsively to a determination using the text based processing that the second computing environment poses reduced security risk relative to the first computing environment.
|