| CPC G06F 21/552 (2013.01) [B60R 25/30 (2013.01); G06F 21/554 (2013.01); G06F 2221/034 (2013.01)] | 17 Claims |
|
1. A security system, comprising:
one or more processors; and
a memory communicably coupled to the one or more processors and storing:
a control module including instructions that, when executed by the one or more processors, cause the one or more processors to:
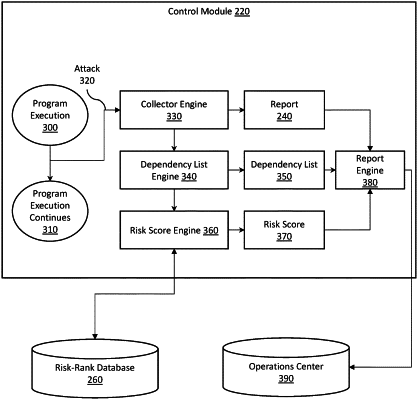
responsive to detecting an attack on a threatened component of a computing system, gather information about the threatened component, including at least a dependency list that specifies related components to the threatened component,
wherein the control module includes instructions to gather the information including instructions to identify information about the threatened component and generate the dependency list by identifying the related components according to interactions with the threatened component, the interactions including at least shared memory, and execution dependencies;
determine a risk score for the attack according to a risk level associated with the attack, a risk type of the threatened component, and combined risks associated with compromising the related components; and
provide a report specifying information about the attack, including at least the risk score.
|