| CPC G06F 21/552 (2013.01) [G06F 2221/034 (2013.01)] | 18 Claims |
|
1. A method comprising:
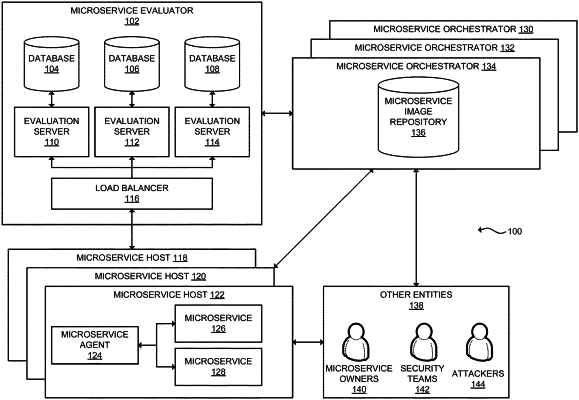
receiving, by a microservice evaluator, from a microservice host, system level activity data corresponding to a plurality of microservices operating on the microservice host, the microservice evaluator being different from, and communicatively coupled to, the microservice host;
training, by the microservice evaluator, a plurality of machine learning models using the system level activity data or a derivative thereof as training data, wherein each machine learning model corresponds to a particular microservice of the plurality of microservices operating on the microservice host;
determining, by the microservice evaluator, using the plurality of machine learning models corresponding to the plurality of microservices and the system level activity data, a plurality of sets of normal system level activities and abnormal system level activities;
determining, by the microservice evaluator, a plurality of security policies corresponding to the plurality of microservices, wherein each security policy comprises a plurality of permitted system level activities and a plurality of non-permitted system level activities;
providing, by the microservice evaluator, to a microservice orchestrator, the plurality of security policies, wherein the microservice orchestrator generates one or more configuration files corresponding to the plurality of security policies and deploys the one or more configuration files to the plurality of microservices operating on the microservice host; and
transmitting, by the microservice evaluator, an instruction to the microservice orchestrator, wherein in response to receiving the instruction, the microservice orchestrator identifies a plurality of microservice owners corresponding to the plurality of microservices and transmits one or more messages to one or more microservice owners of the plurality of microservice owners indicating a change in one or more security policies of the plurality of security policies.
|