| CPC G06F 21/54 (2013.01) [G06F 21/602 (2013.01); G06F 21/6227 (2013.01); H04L 67/56 (2022.05)] | 14 Claims |
|
1. A proxy apparatus for analyzing database queries in a secure network, comprising:
a computer network interface to the secure network;
one or more processing devices operatively connected to the computer network interface; and
one or more memory storage devices operatively connected to the one or more processing devices and having stored thereon machine-readable instructions that cause the one or more processing devices, when executed, to:
receive, in an initial training mode, a plurality of training database queries from one or more computing apparatuses in the secure network via the computer network interface;
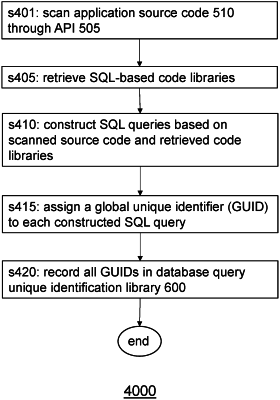
identify at least a query source, a destination database, and a valid-query code for each of the plurality of training database queries, said valid-query code being identified based on one or more predetermined code libraries;
assign a unique identifier for each unique valid-query code identified from the plurality of training database queries, said unique identifier being generated based at least upon a respective first checksum value corresponding to the each unique valid-query code and a predetermined algorithm;
record, in the one or more memory storage devices, the assigned unique identifier, along with one or more unique combinations of the query source and the destination database associated with the each unique valid-query code, to a valid-query library;
receive, in an operational mode, an operational database query from the secure network via the computer network interface;
generate an identifier for the received operational database query based at least upon a second checksum value corresponding to a query code of the received operational database query and the predetermined algorithm;
identify a source and a destination of the received operation database query;
compare the generated identifier, the identified source, and the identified destination to the valid-query library;
when the comparison fails to match any entries in the valid-query library, terminate the operational database query;
when the comparison matches an entry in the valid-query library, relay the received operational database query based on the destination identification via the computer network interface;
identify, in an exception mode, one or more rejected queries associated with an updated application code portion; and
record, in the exception mode, one or more updated unique identifiers corresponding to the one or more rejected queries to the valid-query library,
wherein the comparison comprises comparing a subsequently generated identifier of a subsequent operational database query associated with the updated application code portion to the one or more updated unique identifiers.
|