| CPC G06F 21/32 (2013.01) [G06F 2221/2133 (2013.01)] | 22 Claims |
|
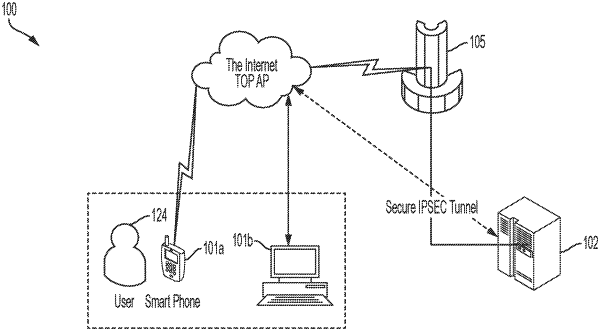
1. A method of authorizing access to access-controlled environments, the method comprising:
receiving, by a computing device, passive authentication information indicative of an identity of an entity;
comparing, by the computing device, the passive authentication information to a stored identifier associated with the entity;
receiving, by the computing device, active authentication information indicative of the identity of the entity;
comparing, by the computing device, the active authentication information to the stored identifier;
generating a liveness evaluation of the entity, including acts of:
validating submission of the passive and active authentication information, wherein the liveness evaluation includes authentication information that validates capture of the passive and active authentication information by a live entity;
processing the authentication information that validates the capture of the passive and active authentication information using a plurality of neural networks including at least a first neural network configured to process passive authentication information and a second neural network configured to process active authentication information;
determining a probability, generated in response to the first and second neural networks processing the passive and active authentication information, that the passive authentication information and the active authentication information are actually obtained from the entity meets a threshold for validation;
receiving, by the computing device, a request from the entity to execute an access-controlled function; and
granting, by the computing device, the request from the entity responsive to determining that an identity probability satisfies a first identity probability threshold associated with the access-controlled function based on, at least in part, the passive and active authentication information and the liveness evaluation.
|