| CPC G06F 12/1036 (2013.01) [G06F 12/145 (2013.01); G06F 21/6254 (2013.01)] | 20 Claims |
|
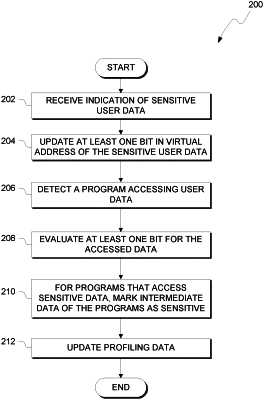
1. A computer-implemented method comprising:
receiving an indication of sensitive data in one or more files;
updating at least one bit in a virtual address space for the one or more files indicated to have sensitive data to mark data in an address range as containing sensitive data;
in response to a program accessing the one or more files, evaluating the respective virtual address for the one or more files;
in response to the evaluation of the at least one bit in the respective virtual address for the one or more files indicating the presence of sensitive data, marking intermediate data generated by the program as sensitive data.
|