| CPC H04W 12/03 (2021.01) [H04L 9/0637 (2013.01); H04L 2209/80 (2013.01)] | 8 Claims |
|
1. A method for implementing secure communication, comprising:
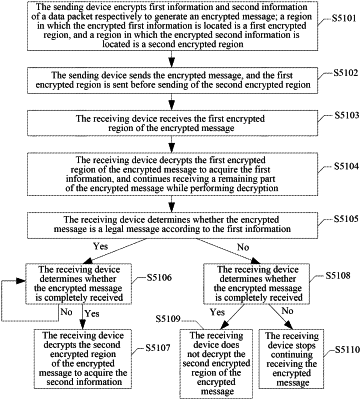
receiving an encrypted message; wherein the encrypted message is generated by encrypting first information and second information of an original data packet respectively, a region in which the encrypted first information is located is a first encrypted region, and a region in which the encrypted second information is located is a second encrypted region; and
decrypting the first encrypted region of the encrypted message, and determining whether to acquire the second information according to the first information after the decryption is successful and the first information is acquired,
wherein:
receiving the encrypted message comprises receiving whole of the encrypted message; or, receiving the first encrypted region of the encrypted message;
receiving the encrypted message comprises receiving the first encrypted region of the encrypted message, and while decrypting the first encrypted region of the encrypted message, the method further comprises continuing receiving a remaining art of the encrypted message; and
determining whether to acquire the second information according to the first information comprises:
when it is determined that the encrypted message is a legal message according to the first information, determining whether the second encrypted region of the encrypted message has been received completely, if the second encrypted region of the encrypted message has been received completely, decrypting the second encrypted region of the encrypted message to acquire the second information; if the second encrypted region of the encrypted message has not been received completely, continuing receiving the second encrypted region of the encrypted message until the second encrypted region of the encrypted message is received completely, and decrypting the second encrypted region of the encrypted message to acquire the second information; and
when it is determined that the encrypted message is not a legal message according to the first information, determining whether the second encrypted region of the encrypted message has been received completely, if the second encrypted region of the encrypted message has been received completely, not decrypting the second encrypted region of the encrypted message; if the second encrypted region of the encrypted message has not been received completely, not continuing receiving the encrypted message.
|