| CPC H04L 63/102 (2013.01) [H04L 63/107 (2013.01); H04L 63/20 (2013.01)] | 20 Claims |
|
1. A system for verifying a request from a user, comprising:
a memory operable to store one or more rules to be satisfied in order to gain access to a plurality of resources, wherein:
the plurality of resources comprises at least one of an application, a database, and a computing device associated with an organization;
each rule of the one or more rules comprises a set of rule attributes indicating conditions to be met by the user so that the user is determined to be eligible to receive an entitlement to access a resource from the plurality of resources;
each rule of the one or more rules is classified into a condition class of a plurality of condition classes; and
the plurality of condition classes comprises a first condition class and a second condition class; and
a processor, operably coupled with the memory, and configured to:
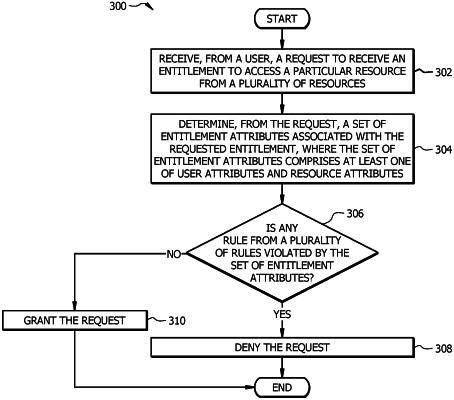
receive, from the user, a request to receive an entitlement to access a particular resource from the plurality of resources;
determine, from the request, a set of entitlement attributes associated with the entitlement indicating a type of permission to access the particular resource, wherein the type of permission comprises at least one of a write-access and a read-access to the particular resource;
determine a first plurality of rules associated with the first condition class;
determine a second plurality of rules associated with the second condition class;
determine, starting at the first condition class and proceeding to the second condition class, whether there is any rule from the first plurality of rules associated with the first condition class and the second plurality of rules associated with the second condition class that is violated by the set of entitlement attributes; and
in response to determining that there is at least one rule that is violated by the set of entitlement attributes, deny the request.
|