| CPC H04L 63/0428 (2013.01) [H04L 9/003 (2013.01); H04L 9/0631 (2013.01); H04L 9/0662 (2013.01); H04L 9/0838 (2013.01); H04L 9/0861 (2013.01); H04L 9/0891 (2013.01); H04L 63/068 (2013.01)] | 10 Claims |
|
1. A data communication encrypted system, comprising:
a plurality of modules including a first module and a second module;
a first network member coupled to the first module; and
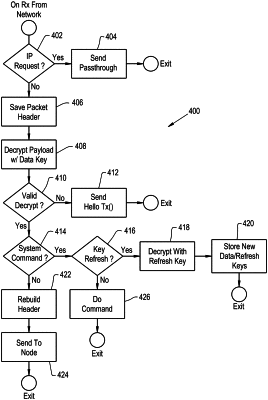
a second network member coupled to the second module, the first module and the second module being in communication with each other thereby allowing communication between the first network member and the second network member, the first module and the second module each operating with a key hopping encryption/decryption method that generates a key set change at irregular intervals of time as determined by the modules, each key set change that occurs at irregular intervals of time being one of a series of key set changes, each of the plurality of modules being configured to generate at least one of the series of key set changes independent of the remaining plurality of modules, a key set being used by the modules to encrypt/decrypt being a current key set, a key set that is generated when a key set change is called for being a new key set, each key set including a data key and a refresh key, the refresh key of the current key set being used to encrypt the new key set before the new key set is sent by the first module or the second module, the refresh key of the new key set being of arbitrary length,
the system being configured to:
append a message with at least one demark character, and padding to make a data set of a selected length, the padding being salt;
initially encrypt the data set using the data key and the salt, until the at least one demark character is encountered; and
encrypt the demark character and the padding using the data key, thereby creating an encrypted data set that is securely communicated from one of the modules to another of the modules.
|