| CPC H04L 9/0822 (2013.01) [H04L 9/0643 (2013.01); H04L 9/30 (2013.01)] | 18 Claims |
|
1. A computer-implemented method comprising:
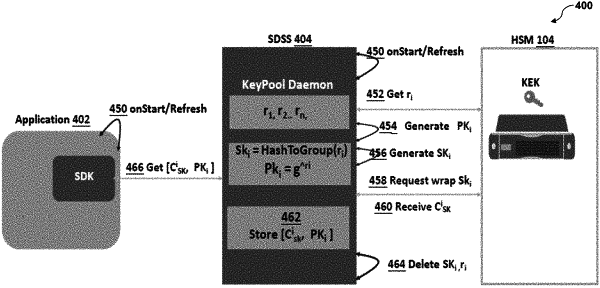
storing, with at least one processor, in memory, a plurality of ciphers (C1, C2, . . . Cn) in association with a plurality of public keys (PK1, PK2, PKn), wherein the plurality of ciphers (C1, C2, . . . Cn) includes a plurality of secret keys (SK1, SK2, SKn) encrypted with a key encryption key (KEK), and wherein the plurality of secret keys (SK1, SK2, SKn) correspond to the plurality of public keys (PK1, PK2, PKn);
receiving, with at least one processor, a data chunk (Mi) for encryption;
generating, with at least one processor, a data encryption key (DEK) based on a hash function (H), a public key (PK1) of the plurality of public keys (PK1, PK2, PKn), and a random number (R);
encrypting, with at least one processor, the data chunk (Mi) with the DEK to generate an encrypted data chunk (CMi);
generating, with at least one processor, a header (Hdr) including a cipher (Ci) of the plurality of ciphers (C1, C2, . . . Cn) corresponding to the public key (PK1) of the plurality of public keys (PK1, PK2, PKn) and key encapsulation data;
storing, with at least one processor, in a database, a cipher text (CT) including the header (Hdr) and the encrypted data chunk (CMi);
receiving, with at least one processor, a request to decrypt the cipher text (CT);
in response to receiving a request to decrypt the cipher text (CT), providing, with at least one processor, to a hardware security module (HSM), the cipher (Ci);
receiving, with at least one processor, from the HSM, a secret key (SK1) of the plurality of secret keys (SK1, SK2, SKn) that corresponds to the public key (PK1) of the plurality of public keys (PK1, PK2, PKn) used to generate the DEK used to generate the encrypted data chunk (CMi);
deriving, with at least one processor, based on the secret key (SK1) received from the HSM and the key encapsulation data, the DEK used to generate the encrypted data chunk (CMi); and
providing, with at least one processor, the derived DEK for decrypting the encrypted data chunk (CMi) to obtain the data chunk (Mi).
|