| CPC H04L 9/0618 (2013.01) [G06F 9/5016 (2013.01); G06F 12/121 (2013.01); G06F 12/1408 (2013.01); G06F 12/1441 (2013.01); G06F 12/1458 (2013.01); G06F 2212/7207 (2013.01)] | 25 Claims |
|
1. A processor, comprising:
a register to store a first encoded pointer for a first memory allocation for an application; and
circuitry coupled to a memory, the circuitry to:
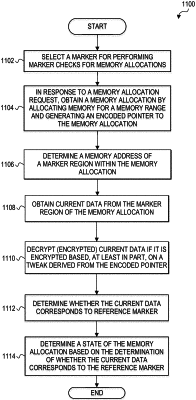
determine a first memory address of a first marker region in the first memory allocation;
obtain current data from the first marker region at the first memory address;
compare the current data to a reference marker stored separately from the first memory allocation;
determine that the first memory allocation is in a first state based on a determination that the current data corresponds to the reference marker; and
based on the first memory allocation being in the first state, prevent access to contents currently stored in the first memory allocation.
|