| US 11,783,341 B1 | ||
| System and method of identifying fraud indicators within telecommunications networks | ||
| Michael A. Gailloux, Overland Park, KS (US); and Lauren Ricardo St. Aubyn King, Somerset, NJ (US) | ||
| Assigned to T-MOBILE INNOVATIONS LLC, Overland Park, KS (US) | ||
| Filed by T-Mobile Innovations LLC, Overland Park, KS (US) | ||
| Filed on Oct. 13, 2015, as Appl. No. 14/882,064. | ||
| Int. Cl. G06Q 20/32 (2012.01); G06Q 20/40 (2012.01); H04W 12/12 (2021.01); H04W 8/18 (2009.01); H04W 12/06 (2021.01); H04L 9/40 (2022.01) | ||
| CPC G06Q 20/4016 (2013.01) [G06Q 20/3227 (2013.01); H04L 63/0876 (2013.01); H04W 8/18 (2013.01); H04W 12/06 (2013.01); H04W 12/12 (2013.01)] | 7 Claims |
|
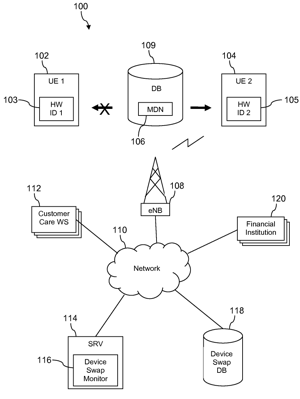
1. A method of mitigating identity theft based on monitoring mobile communication device identity swapping, comprising:
storing information about requests to transfer a mobile communication device credential between different mobile communication devices in a device swap data store by a computer system; receiving, by the computer system, a request to transfer a mobile communication device credential from a first mobile communication device to a second mobile communication device; in response to receiving the request and prior to transferring credentials between the first mobile communication device and the second communication device:
determining, by the computer system, an identity of the first mobile communication device;
determining, by the computer system, an identity of the second mobile communication device;
looking up, by the computer system in the device swap data store, information about requests to transfer credentials based on the identity of the first mobile communication device and on the identity of the second mobile communication device; and
determining, by the computer system, that a number of requests to transfer credentials associated with at least one of the first mobile communication device or the second mobile communication device exceeds a predefined number of credential transfers per period of time, the determination being an indicator of potential fraud by a user providing the request to transfer the mobile communication device credential from the first mobile communication device to the second mobile communication device; and
based on determining that the number of requests exceeds the predefined number of credential transfers, taking action by the computer system. |