| CPC G06F 21/6245 (2013.01) [G06F 21/53 (2013.01); H04L 9/08 (2013.01); H04L 9/0894 (2013.01); H04L 9/3236 (2013.01); H04L 63/06 (2013.01)] | 20 Claims |
|
1. At least one non-transitory computer-readable medium comprising instructions that, if executed by a processor, enable a computer to:
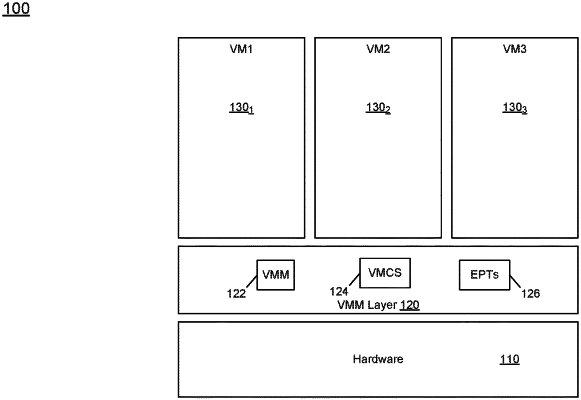
receive a domain manager image and memory position-dependent address information in response to requesting a service from a cloud services provider, wherein the domain manager image comprises computer code to provide virtual machine monitor (VMM) functionality;
verify the domain manager image;
identify a key domain key to be used to encrypt data stored in a key domain of a key domain-capable server, wherein the key domain comprises a plurality of memory locations of a memory of the key domain-capable server;
use the key domain key and the memory-position dependent address information to encrypt a domain launch image such that the encrypted domain launch image is cryptographically bound to at least one memory location of the key domain;
encrypt the key domain key; and
send the encrypted domain launch image and the encrypted key domain key to the key domain-capable server, to cause a processor of the key domain-capable server to execute an instruction to create the key domain.
|