| CPC G06F 21/577 (2013.01) [G06F 2221/034 (2013.01)] | 9 Claims |
|
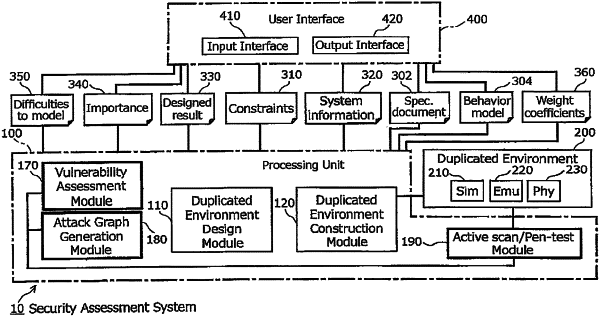
1. A security assessment system configured to provide a duplicated environment which duplicates an assessment target system comprising a plurality of physical components, the security assessment system comprising:
a duplicated environment design circuitry configured to select a duplication level for each physical component based on constraints specified by a user and a duplicated priority associated with the physical components in order to design the duplicated environment to produce a designed result indicative of duplicated environment design, the duplication level being indicative of any one of a simulation sub-module, an emulation sub-module, and a physical sub-module which are for reproducing the physical components of the assessment target system; and
a duplicated environment construction circuitry configured to construct the duplicated environment based on the designed result, the duplicated environment comprises components which are duplicated by one of duplication levels,
wherein the constraints comprise at least one selected from the group consisting of budget and time, and
wherein the duplicated environment design circuitry is configured to select the duplication level for each physical component that satisfies a condition that required cost doesn't exceed the budget or required time doesn't exceed the time based on the duplicated priority of each physical component that is determined based on at least one selected from the group consisting of importance of each physical component, potential to refine a security diagnosis, and difficulties to model each physical component.
|