| CPC G06F 21/57 (2013.01) [G06F 9/44505 (2013.01); G06F 9/45504 (2013.01); G06F 21/64 (2013.01); G06F 30/20 (2020.01); H04L 63/08 (2013.01); H04L 67/34 (2013.01)] | 10 Claims |
|
1. A method for computer-aided executing of an application in a trusted execution environment, the method comprising:
providing configuration data for executing the application;
transmitting the configuration data to an authentication service;
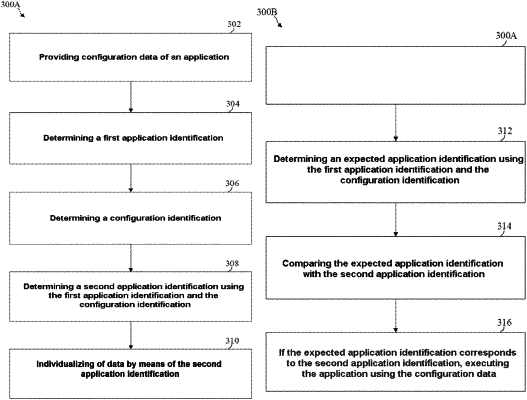
determining a first application identification, wherein the first application identification is assigned to the application, wherein determining the first application identification comprises receiving of an execution request of the application by a start service, wherein the start service determines the first application identification is determined using the execution request;
the start service transmitting a configuration identification demand to the authentication service for demanding a configuration identification from the authentication service;
in response to receiving the configuration identification demand, the authentication service determining the configuration identification comprising a first authentication identification, which is assigned to the configuration data of the application, and a second authentication identification, which is assigned to the authentication service, and transmitting the configuration identification to the start service;
the start service generating the trusted execution environment in response to receiving the configuration identification, wherein the first authentication identification is assigned to the trusted execution environment;
individualizing the data by means of a second application identification, wherein the second application identification is determined by the start service using the first application identification and the configuration identification, wherein the second application identification is an identifier of the generated trusted execution environment, and wherein the second application identification is assigned to the application and the configuration data of the application;
the start service starting an execution environment service being executed in the trusted execution environment;
the execution environment service transmitting a configuration data demand to the authentication service for demanding the configuration data for executing the application, wherein the configuration data demand comprises the second application identification;
in response to receiving the configuration data demand, the authentication service determining an expected application identification using the first application identification and the configuration identification, comparing the expected application identification with the second application identification and, if the expected application identification corresponds to the second application identification, transmitting the configuration data to the execution environment service; and
the execution environment service executing the application in the trusted execution environment using the configuration data.
|