| CPC G06F 11/1458 (2013.01) [G06F 21/64 (2013.01); H04L 9/0643 (2013.01); G06F 2201/84 (2013.01)] | 20 Claims |
|
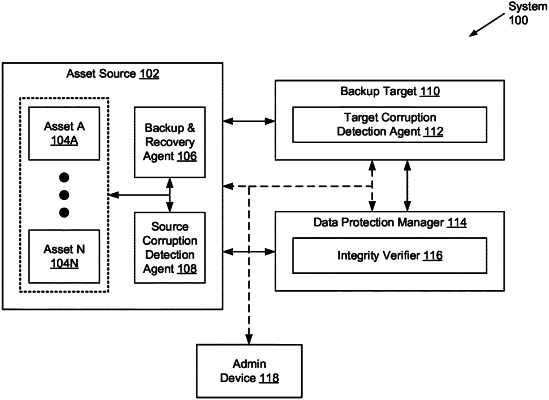
1. A method for data protection, comprising:
providing, to an asset source, instructions for initiating a backup operation targeting asset data of an asset on the asset source;
receiving, from the asset source and in response to the instructions, source backup information indicating a state of the asset data prior to initiation of the backup operation by the asset source;
receiving, from a backup target, a backup transferred notification informing that the backup target has received a completed transfer of an asset backup representing a copy of the asset data from the asset source by way of the backup operation;
submitting, to the backup target and based on receiving the backup transferred notification, a target backup information request comprising an information mode;
receiving, from the backup target and in response to submission of the target backup information request, target backup information indicating a state of the asset backup;
making a determination that the asset backup, having arrived at the backup target, is corruption-free based on the state of the asset data matching the state of the asset backup; and
instructing, based on the determination, the backup target to commit the asset backup.
|