| CPC G06F 21/602 (2013.01) [G06F 21/31 (2013.01); G06F 21/577 (2013.01)] | 17 Claims |
|
1. A system for providing complex data encryption, the system comprising:
at least one non-transitory storage device; and
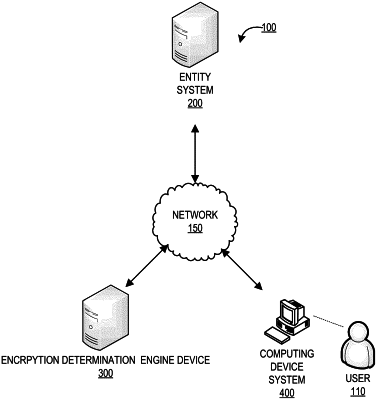
at least one processing device coupled to the at least one non-transitory storage device, wherein the at least one processing device is configured to:
receive a user input code from a computing device associated with a user, wherein the user input code is one or more plaintext characters;
generate a first encrypted value using a first encryption algorithm based on the user input code;
decrypt the first encrypted value using one or more additional encryption algorithms, wherein one or more synthetic user input codes are generated by the decryption of the first encrypted value using each of the one or more additional encryption algorithms;
determine a first encryption vulnerability score based on the value of the one or more synthetic user input codes, wherein the first encryption vulnerability score is based on one or more similarities between the user input code and the one or more synthetic user input codes;
cause a transmission of a user input code notification based on the first encryption vulnerability score;
generate a second encrypted value using a second encryption algorithm based on the user input code,
decrypt the second encrypted value using the one or more additional encryption algorithms, wherein one or more secondary synthetic user input codes are generated by the decryption of the second encrypted value using each of the one or more additional encryption algorithm; and
determine a second encryption vulnerability score based on the one or more secondary synthetic user input codes.
|