| CPC H04L 63/205 (2013.01) [G06F 16/2365 (2019.01); G06F 16/908 (2019.01); G07C 9/00 (2013.01); G07C 9/21 (2020.01); G07C 9/215 (2020.01); G07C 9/23 (2020.01); H04L 63/08 (2013.01); H04L 63/10 (2013.01); H04W 12/08 (2013.01); H04L 63/0823 (2013.01); H04L 63/0838 (2013.01); H04L 2463/121 (2013.01); H04W 12/06 (2013.01); H04W 12/61 (2021.01)] | 2 Claims |
|
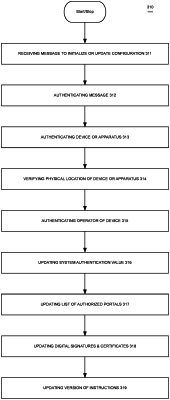
1. A method for control of a physical access portal comprising the processes: at a controller,
receiving a plurality of physical access requests (access requests) from a plurality of mobile application devices; at the controller,
determining for each mobile application device (app device) a sequence of access requests comprising at least a first access request and a second access request SOLELY GENERATED BY EACH mobile application DEVICE; at the controller, upon authenticating the first access request (predecessor), writing into non-transitory storage a one-time verification code specific to an immediately subsequent second access request (successor) from the same mobile application device; and at the controller,
upon receiving a successor, performing an authentication process by matching the stored one-time verification code associated with the predecessor; and
on the condition the authentication process passes, writing a newer one-time verification code into non-transitory storage specific to yet another immediately subsequent successor;
wherein each newer one-time verification code is synthesized WITH A MASK OF LEAST SIGNIFICANT BITS TO PROVIDE A RANGE OF TIME RELATING A REQUEST AND THE LAST SUCCESSFUL PHYSICAL ACCESS REQUEST SOLELY AT AND by the mobile application device and transmitted in both a predecessor and successor request; and,
on the condition the authentication process fails,
setting a flag of questionable chain of control associated with the mobile application device.
|